You would think after the Ashley Madison incident, where nearly 37 million cheating men and women had their data stolen, sites like Adult Friend Finder would up their cybersecurity. Wrong! On Sunday…
RATs Everywhere
Remote Access Trojans, or RATs for short, are malicious programs that run invisibly on host PCs and permit an intruder remote access and control. On a basic level, many RATs mimic the functionality…
Cybersecurity Spending to Top $100 Billion by 2020
With the growing fear of becoming the next victim of a cyberattack, companies are taking major precautions and upping their cybersecurity. Research firm International Data Corporation (IDC) recently…
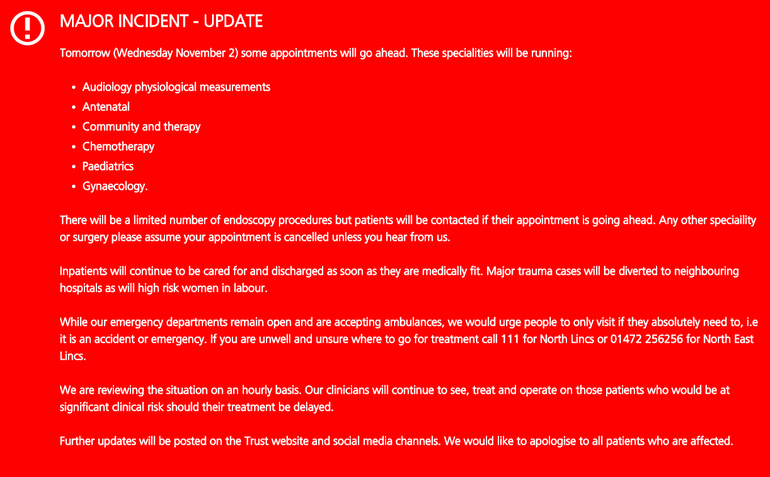
UK Hospitals Hit by Cyberattack
The Northern Lincolnshire and Goole NHS Foundation Trust were hit by a cyberattack on Sunday, October 30th. The computer virus forced the three hospitals in its organization to go offline and caused…
Anatomy of Ransomware
A little over a decade ago, most computer viruses were simpler than the ones we see today. Back then viruses were like a 3 function Swiss army knife; they might change the background, rename files,…
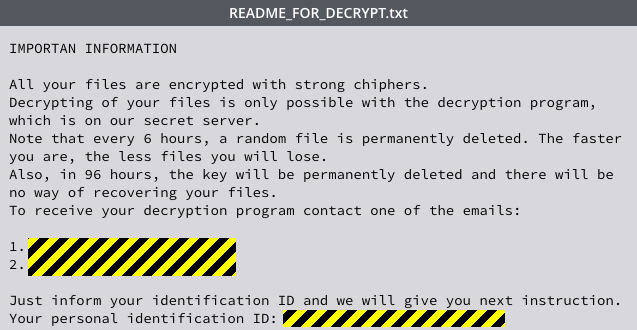
Here Comes CryPy Ransomware
Ransomware has been all over cybersecurity headlines for the last ten months. This week’s feature is CryPy, a form of ransomware that is adding a spin to how files are encrypted and the ransom…
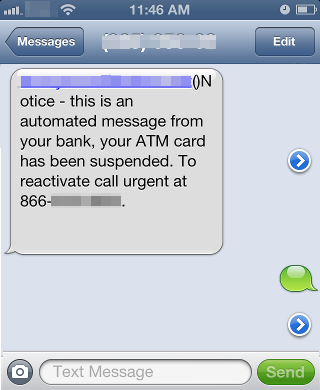
Smishing - Phishing's New Bait
Chances are, you have been receiving an onslaught of calls from automated voices saying they can lower your credit card interest rates or that you have randomly won a cruise. Apparently, the ‘do not…
Why Ransomware Attackers Really, Really Like Cloud Computing
Ransomware attacks are on the rise, and it is just a matter of time before a major attack is launched. So, businesses should take proper precautionary measures. A ransomware attack can disrupt all…
Ransomware is a growing security threat among businesses, home, and government networks. Thus, it is crucial for everyone who runs a network to understand the preventive measures they can take…