One of the fastest growing cyber threats is ransomware. Ransomware is malware that installs covertly on a victim's computer, executes a encryption attack, and demands a ransom payment to restore the…
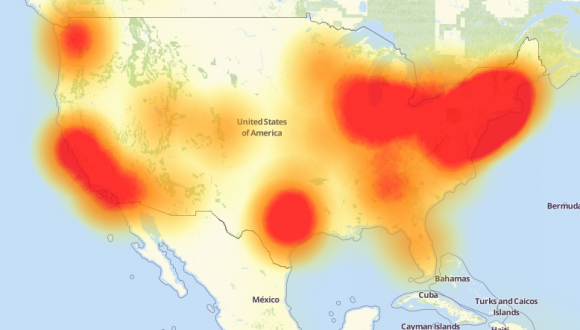
Mirai Botnet Responsible for Largest DDoS Attack
Twitter, Reddit, Spotify, Etsy and what seems like an endless list of websites were down for an extended amount of time on Friday (Oct. 21) due to a Distributed Denial of Service (DDoS) attack on…
What To Do If Infected with Ransomware
Ransomware is a type of malware that targets your most important data for the sole purpose of extortion. Once the cyber attacker has access to the data and administration system, they demand a ransom…
Deception Technology As A Key Emerging Security Technology
Cybersecurity threats evolve daily. As such, network security providers must be aware of the threat and respond in kind with more sophisticated and deeper ways of addressing security issues. A new…
How a Popular Bitcoin Site Could Have Prevented The Attack on Their Site
A popular Bitcoin transaction site known as blockchain.info suffered a temporary DNS attack. The company’s internet properties were subjected to rogue control for the duration of the attack on the…
Tip of the Week – A Free Tool For Testing Anti-Ransomware Defenses
We have written two PowerShell scripts that function just like ransomware. One script encrypts the data, and the other script decrypts the data using a public/private key pair. We created these as a…
How to Check if You've Been Affected by the Yahoo Hack
As some reading this may know, the Yahoo hack happened last month. Sources are starting to state that this may be the biggest hack in history. A state-sponsored actor sparked a network security…
What is Endpoint Detection and Response (EDR)?
Talk to any security expert in the field who has a few years of experience under their belt, and they will tell you the current threat landscape is ever-evolving and it takes a lot of effort and…
Types of Social Engineering
As the CEO of WatchPoint, I believe marketing our products is an extremely important part of the success of our business. We want our customers to be aware of the many ways we can protect their…