The year was 2000. I was in college, and I can remember it vividly: moving from place to place and hauling around my stack of all-powerful 200MHz computers that were my prized lab computers. That all…
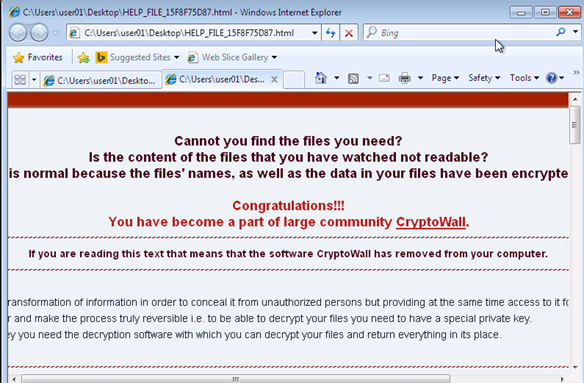
The Life of IT: CryptoWall
From one IT professional to another, I understand your frustrations all too well. I’ve been there, for 16 years now. One day you walk into work, and everything is blissful. And on the next, some…
Malware: Coming of Age
Malware, short for malicious software, covers any infectious file on a computer system. Common examples are viruses, worms, Trojan horses, and ransomware. Throughout the decades, these mal-intended…
Tips to Help Stop a Brute-force Attack
A brute-force attack is a common threat faced by web developers where an attacker attempts to crack a password by systematically trying every possible combination of letters, numbers, and symbols…
The Established Threat of Passwords
Passwords, passwords, and more passwords; this is normally the subject that websites, technology help staff, network administrators, and other computer related experts will harp on the most. I am…
Locking Your Kid's Credit
It’s the year 2030 and your son, James, is off to get his first car. With a sparkle in his eyes and an extra pep in his step, he heads to his local bank to secure a loan for the first big purchase on…
Fast Facts Regarding Linux Root User
If you are new to Linux you may have a few questions about the root user and its intended use. It’s imperative that you understand when you should or shouldn’t use the root account and the dangers of…
When Failure to Act Results in a Compromised Network – A Sad Cryptolocker Tale
I’d like to discuss a situation that arose this week with a former backup customer and how that customer came to realize they need WatchPoint. For privacy concerns, I will address the business as…
Ransom32: The First JavaScript Ransomware
Security researchers have found a new ransomware-as-a-service (RaaS) using JavaScript (JS) framework called NW.js. The new RaaS, tabbed as Ransom32, is different from other RaaS attacks as it is…