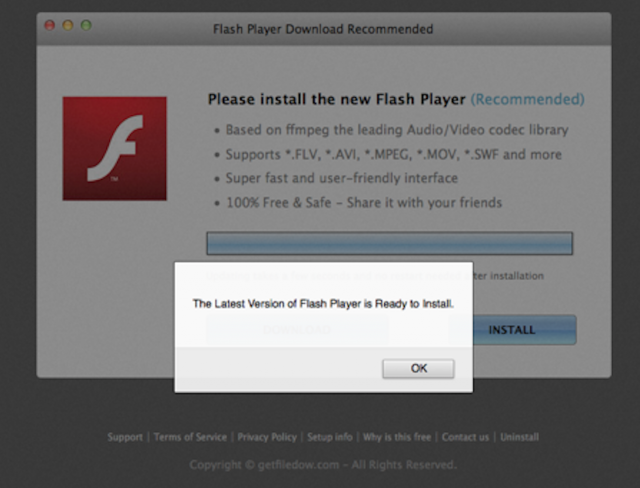
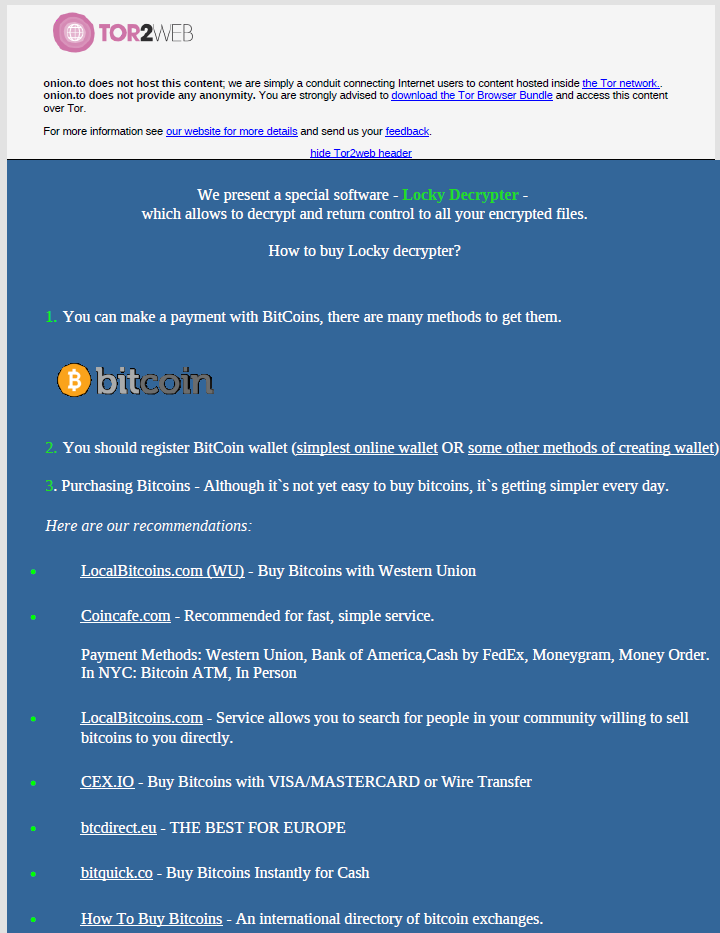
With the daily emergence of new hacking tools such as cryptowall, ransomware and phishing attacks, it looks like hackers are hoping you forgot about a common mistake some may make daily; typing…
Ransomware: The Threat is Real
2016 will be remembered as the year of Ransomware. We have already seen two major hospitals literally shut down for days by cyber criminals that held their data hostage, including patient records.…
Assume Breach - A New Approach To Security
Traditional computer security has focused on protecting the perimeter. While this is still a vital practice, focusing on this alone has ultimately proved unsuccessful. Day after day, high profile…
Gone Phishing: Why Human Resources is Vulnerable to Crypto Ransomware Attacks
I recently received an email that came into our ticketing system which at first glance seemed to be a woman submitting a resume to WatchPoint. The email was simple and introduced Charlotte Roye, who…
Another Hospital Becomes Victim of Ransomware
A little over a month after Hollywood Presbyterian Medical Center became the victim of a ransomware attack, Methodist Hospital in Henderson, Kentucky has issued an “internal state of emergency” to…
Why Didn’t My AntiVirus Detect Cryptowall….again!?
I’ve previously written an article about why antivirus (AV) software has such a difficult time detecting cryptolocker, cryptowall, and other ransomware when it infects a network. I had expected that…
Lock Down Exchange from Brute-Force Attack
A brute-force attack is a common threat faced by web developers where an attacker attempts to crack a password by systematically trying every possible combination of letters, numbers, and symbols…
Defenseless Against Cryptowall…Or Are We?
You enter work on a bright Monday morning with several projects on your plate: clients to call, appointments to make, accounts to update, meetings with staff. But what you weren’t expecting was to…
Threat Detection For The On-the-Go Workforce
When I started my first corporate IT job in 2000, maybe 25 of the 500 end users I supported had laptops. I’m no longer in IT management, but I still know people in the biz. Today, it is a much…