Personally Identifiable Information (PII) is defined as any information that can be used on its own or combined with other information to identify, contact or locate an individual. This can include…
The Comeback of the Honeypot
A Brief History of the Honeypot No, not the organic, non-gmo, honey we all love. Today we're talking about Honeypot computer systems.
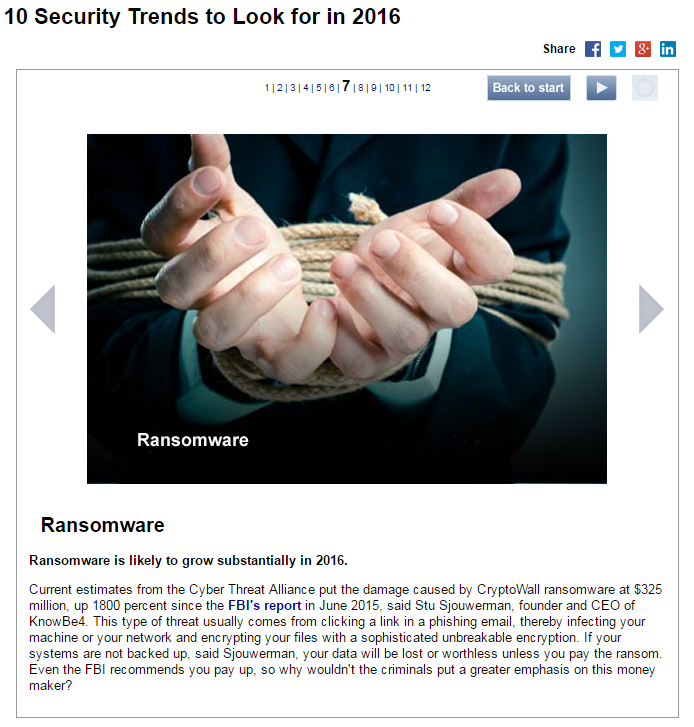
Ransomware 2.0: What's Next?
In 2015, security experts were predicting ransomware would be huge for cybercriminals in 2016. The majority had no idea it would be this huge.
Introducing CryptoStopper
Cybercriminals have a large toolbox when it comes to Ransomware. There are many different variants of Ransomware, but they all have the same intent – to encrypt your data and hold it for a financial…
Kansas Heart Hospital in Wichita was the latest in a string of hospitals around the country to be hit with ransomware. The amount of the ransom request is unknown, but we do know that the hospital…
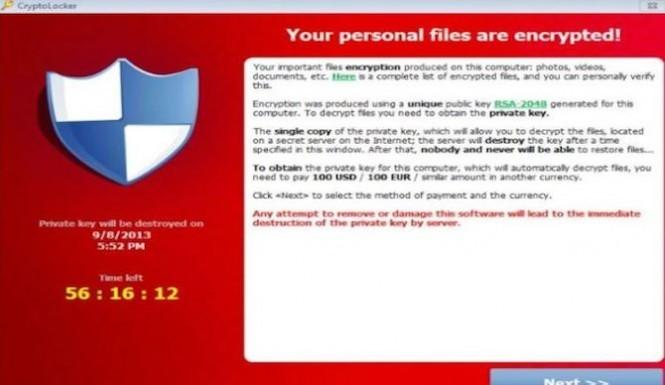
TeslaCrypt Encryption Key Released
Recently an odd turn of events occurred in the ransomware industry. The developers of TeslaCrypt shut down, seemingly on their own. The surprising thing was that they also released a master…
You come into work Monday morning after a wonderful weekend with the family and are ready to start the week off with a bang. Meetings scheduled, appointments set, clients to contact, but first you…
The security experts at WatchPoint are vigorously working to get ahead of ransomware. We constantly analyze new strains of ransomware, banking Trojans, and malware and have created a product called…
Employees: The Weakest Link in Cybersecurity
From day one, we have said that employees are the weakest link in the cybersecurity chain for an organization. In a recent webcast, Michael Gelles and Robert McFadden of Deloitte Consulting LLP…