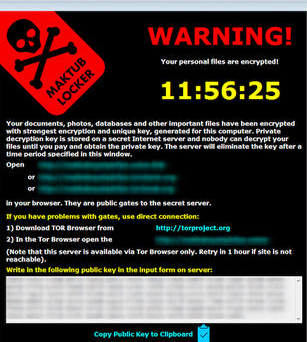
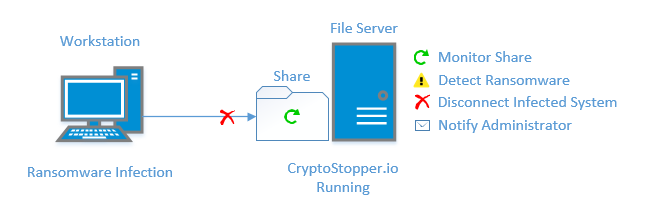
It seems every week we are writing about the “newest” ransomware threat. The first ransomware variants encrypted your files and demanded small ransoms from $50 to $250 to decrypt files. Today…
Ransomware, and the Big Heist
The word - Ransomware. It’s an interesting word. The first half being ransom- as in, to hold for ransom; and the second half -ware, as in, software; ransom-software. As with any ransom, there are…
Sextortion is the act of extorting money from someone using the threat of sharing sexually explicit photos or videos that were obtained by illicit means. The photos and videos used in the extortion…
Watchpoint (New) Intro Video
In a continuing effort to educate our customers and to bring understanding to the value that advanced cybersecurity techniques can bring to the table, we’ve created a new Introduction video. In the…
FBI Releases Article on Ransomware
You know things are getting serious when the Federal Bureau of Investigation (FBI) releases an article on a situation. On Friday (April 29th, 2016), the FBI released an article titled “Incidents of…
Dell released a SonicWall Security Center alert regarding the Jigsaw ransomware virus on April 22, 2016. The alert explained that “The Dell SonicWall Threats Research team has received reports of a…
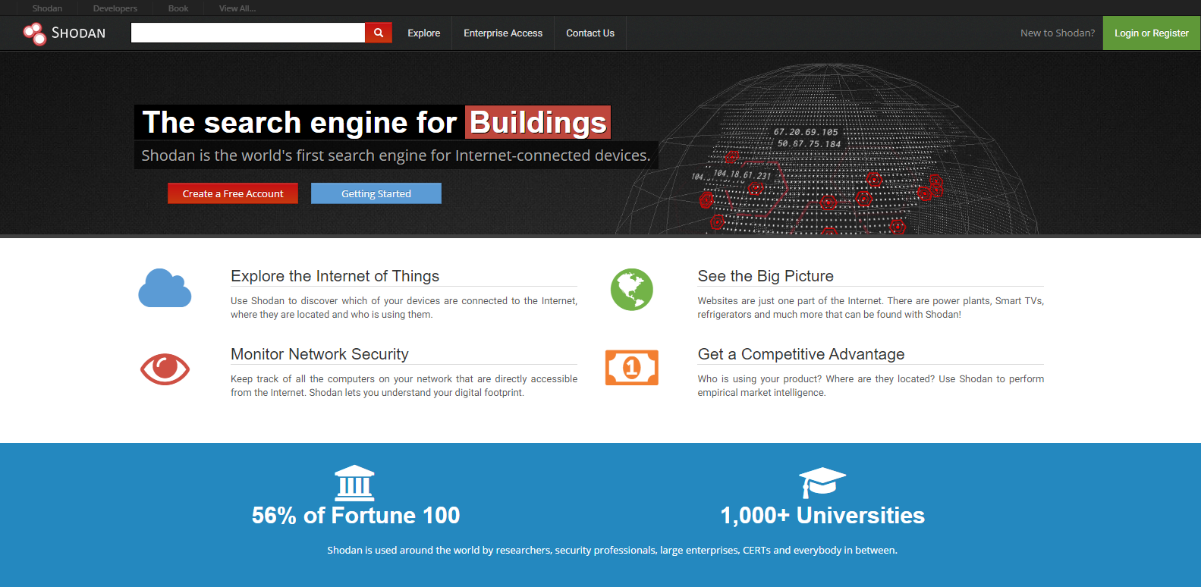
Shodan Demonstrates Why Closing Unused IoT Ports is Critical to Cyber Security
The Internet of Things (IoT) is defined as the vast network of physical objects like cell phones, vehicles, doorbells, and entire buildings that are embedded with electronics, software sensors, and…
2016 Cyber Security Statistics
The first quarter of 2016 has seen a significant rise is cyberattacks, and unfortunately, the forecast doesn’t look much better. Banking Trojans and Ransomware have dominated the cyber security stats…
How to Deceive Hackers into Exposing Themselves
We’ve seen it acted out a hundred times on the big screen. The tough-talking cop, who towers over the newly arrested suspect, hands still cuffed behind their back, as the bright lights of justice…