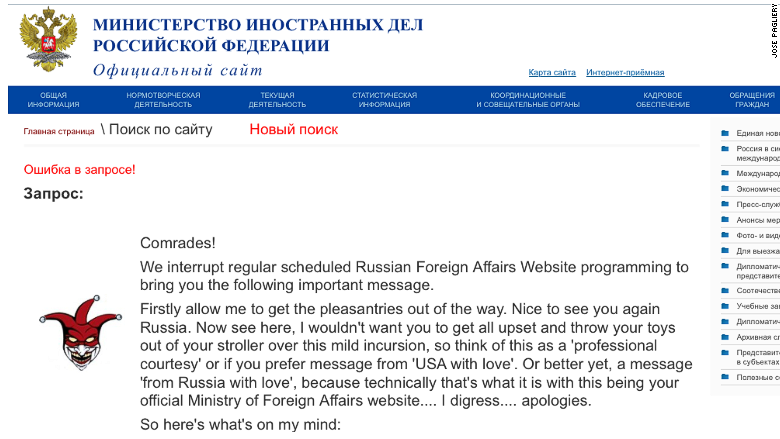
An American hacker who goes by the name of “Jester” has struck back against the Russian federation in retaliation for Russian cyber-attacks against American companies and the recent cyber-attack…
Adult Friend Finder Exposed in Latest Breach
You would think after the Ashley Madison incident, where nearly 37 million cheating men and women had their data stolen, sites like Adult Friend Finder would up their cybersecurity. Wrong! On Sunday…
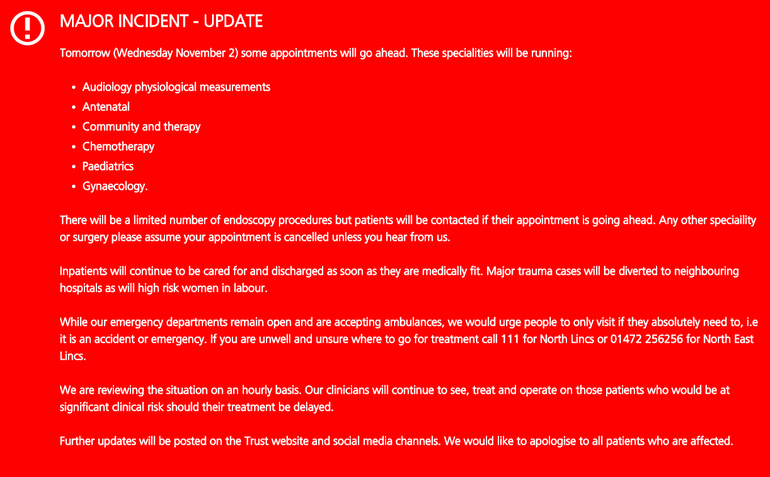
UK Hospitals Hit by Cyberattack
The Northern Lincolnshire and Goole NHS Foundation Trust were hit by a cyberattack on Sunday, October 30th. The computer virus forced the three hospitals in its organization to go offline and caused…
What is Endpoint Detection and Response (EDR)?
Talk to any security expert in the field who has a few years of experience under their belt, and they will tell you the current threat landscape is ever-evolving and it takes a lot of effort and…
Three Common Ways Ransomware Enters Your Network
Ransomware attacks have ratcheted up significantly since the first quarter of 2016 as more and more cybercriminals attempt to extort money from victims by using ransomware to encrypt their data and…
Best Ransomware Protection
Tips to Improve Network Security Loss of productivity due to ransomware attacks is on the rise and cybercriminals are cashing in, making millions of dollars with minimal investment and effort.…
The Top 8 Digital Marketing Trends for Law Firms in 2016
In the recent past, competition in the legal sector has taken a new dimension. There are more lawyers than there were ten years ago and they all want to build successful law firms. As such, legal…
Voter Databases Breached in Illinois and Arizona
Ahead of the November 8th presidential election, the Federal Bureau of Investigation (FBI) is urging states to increase computer security. This comes as no surprise with the recent breach of election…
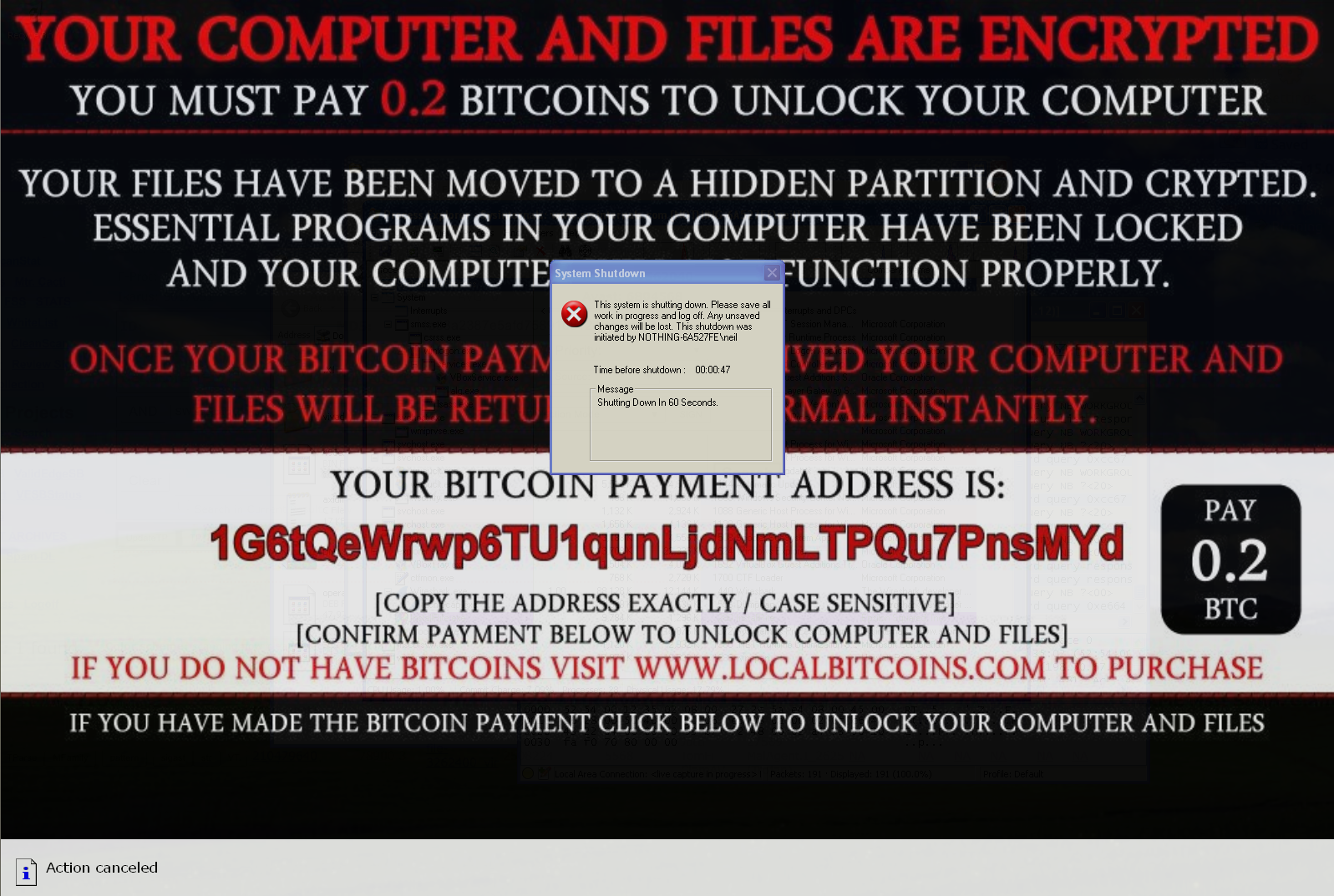
Another week has gone by, and yet another cryptographic ransomware variant has emerged. The latest ransomware discovery has many in the industry concerned because it is rare for a cybercriminal to…