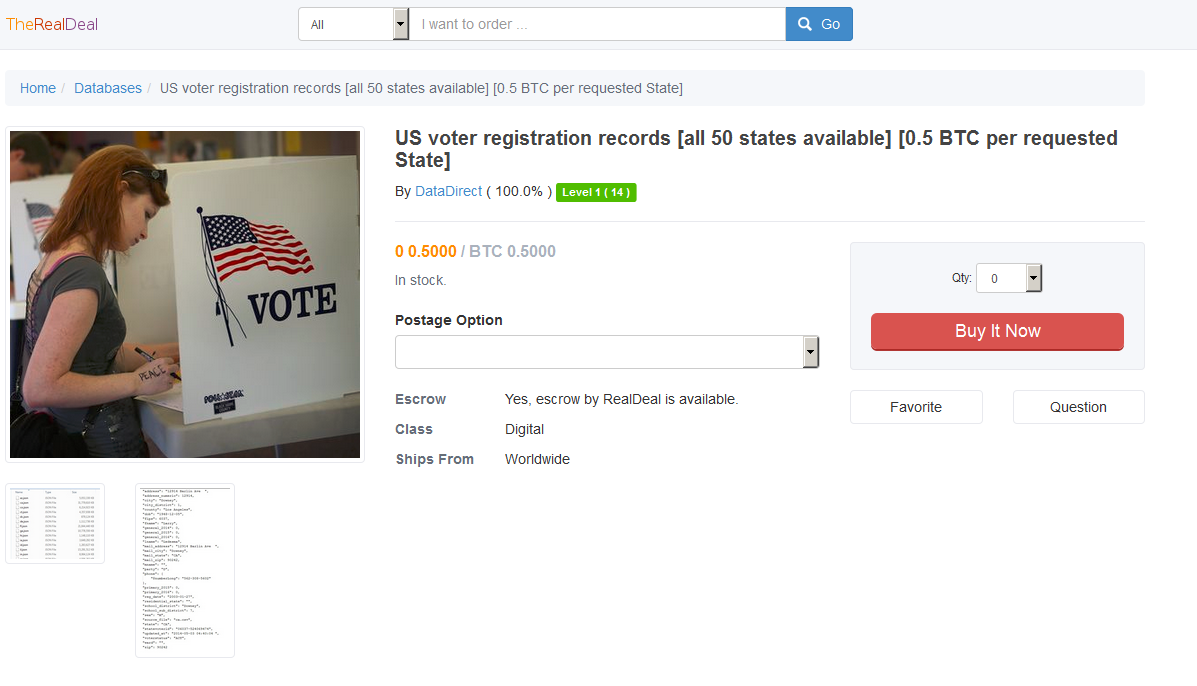
As if we do not already have enough to worry about in the upcoming U.S. election, now hackers have access to the entire U.S. Voter Registration database. A seller going by the handle “DataDirect” on…
Back in early January, we gave you a prediction for the Top 7 Cyber Crime Threats for 2016. Now that we are just over half of the way through the year, we thought we would revisit that article and…
What is Deception Technology?
Set a Trap to Catch Cybercriminals Deception Technology is a new approach to cybersecurity that is designed to prevent a cybercriminal who has already infiltrated a network from doing damage. This…
What can you learn from DNC's recent hack?
Two different hacker groups were on the DNC servers for months, undetected. It is assumed that the hack originated from a phishing campaign with a malware payload. CrowdStrike was used after the fact…
Cerber Avoids Detection The latest strain of Cerber ransomware has been upgraded to morph every 15 seconds to avoid detection. Traditional AV can't update quick enough to keep up. 12M to 16M new…
Over 400 Million Affected in Latest Hacks
Myspace and Tumblr have become the latest victims of a data breach, with over 400 million email addresses, usernames, and passwords stolen in the last month.
EDR | EndPoint Detection and Response
Why do breaches continue to happen? Companies are spending billions of dollars to prevent data breaches, yet they are still occurring every day. In all of the recent major breaches, forensic evidence…
Ransomware and Data Theft
It is only a matter of time until we start hearing the news stories of ransomware attackers combining data theft into the equation. Currently, the only stories about threats and data have been highly…
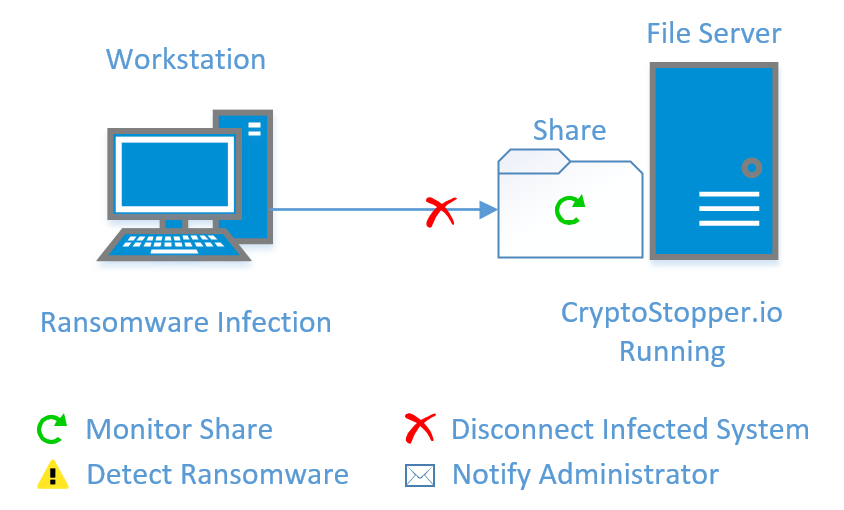
How to Protect Personally Identifiable Information from Ransomware Attacks
Personally Identifiable Information (PII) is defined as any information that can be used on its own or combined with other information to identify, contact or locate an individual. This can include…