Recently an odd turn of events occurred in the ransomware industry. The developers of TeslaCrypt shut down, seemingly on their own. The surprising thing was that they also released a master…
The security experts at WatchPoint are vigorously working to get ahead of ransomware. We constantly analyze new strains of ransomware, banking Trojans, and malware and have created a product called…
Employees: The Weakest Link in Cybersecurity
From day one, we have said that employees are the weakest link in the cybersecurity chain for an organization. In a recent webcast, Michael Gelles and Robert McFadden of Deloitte Consulting LLP…
Past Due Bill or Ransomware?
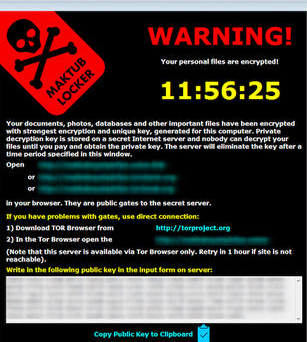
It seems every week we are writing about the “newest” ransomware threat. The first ransomware variants encrypted your files and demanded small ransoms from $50 to $250 to decrypt files. Today…
Sextortion is the act of extorting money from someone using the threat of sharing sexually explicit photos or videos that were obtained by illicit means. The photos and videos used in the extortion…
With the Dyre Banking Trojan going silent or being completely shut down in early 2016, we shouldn’t be surprised that other banking Trojans have emerged. Android/Spy.Agent.SI and GozNym have been the…
Why Didn’t My AntiVirus Detect Cryptowall….again!?
I’ve previously written an article about why antivirus (AV) software has such a difficult time detecting cryptolocker, cryptowall, and other ransomware when it infects a network. I had expected that…
Tips to Help Stop a Brute-force Attack
A brute-force attack is a common threat faced by web developers where an attacker attempts to crack a password by systematically trying every possible combination of letters, numbers, and symbols…
How Many of Your Employees Will Get Phished Today?
Phishing is an attempt by cybercriminals to steal your money and data using malicious email messages, websites and sometimes even phone calls. These criminals gain access to your information by…