March was a month where a lot of small ransomware variants appeared but never came to fruition. There was, however, an update on CryptoLocker making its return, Cerber added a couple of new features,…
A zero-day attack named Double Agent has been discovered that exploits a 15-year-old feature in Windows from XP through Windows 10. The attack has the ability to take over antivirus software on…
Spear Phishing Examples
Phishing is one of the most common attack vectors hackers use to initially infiltrate a user’s system. Phishing is an attempt to obtain user credentials, financial data, or other sensitive…
Top 7 Revelations of Vault 7
WikiLeaks dropped a bombshell on Tuesday, March 7th when it began a new series of leaks on the U.S. Central Intelligence Agency. Code-named Vault 7, Year Zero is the first series and is comprised of…
Advanced Persistent Threats and Ransomware
Advanced Persistent Threats (APT) and ransomware have been the most dreaded types of malware over the last couple of years. While there are clear and distinct differences between APTs and ransomware,…
February Ransomware in Review
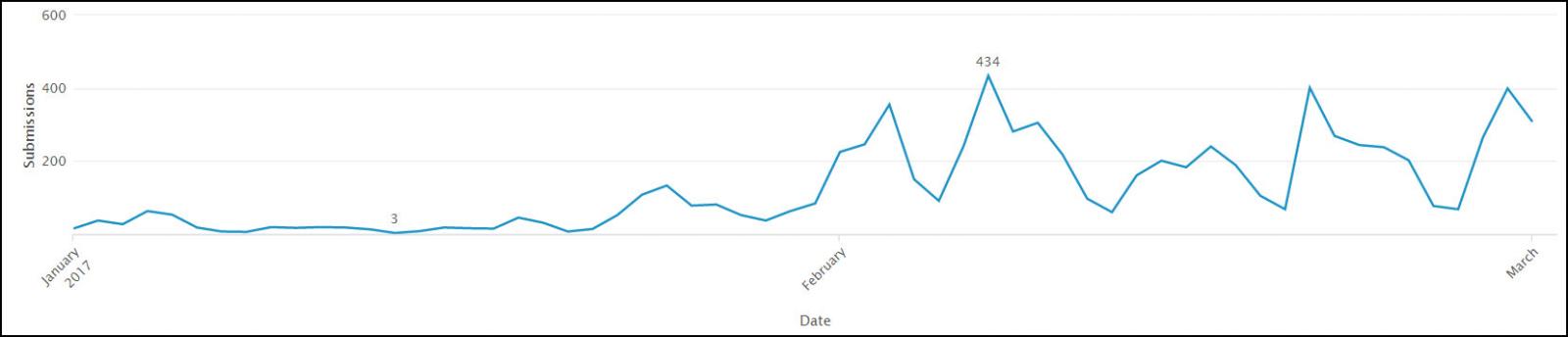
Although February was a short month, there certainly wasn’t a shortage of new ransomware variants. While there were several variants that will probably never make it into circulation, there was some…
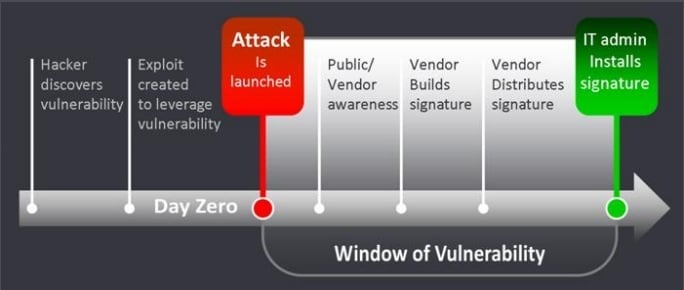
Zero-Day Attack Examples
Stuxnet is known as the world’s first cyber weapon. Stuxnet was used to break Iran’s uranium enrichment centrifuges when it was feared they were producing chemical weapons. While there’s no proof as…
BEWARE: You Can be Sued for Cybersecurity Negligence
In this day and age, it seems like you can sue or be sued for almost anything. Now, a company is being sued for cybersecurity negligence. That’s right; you can be sued for not having proper…
PlayStation and Xbox Users Hacked
The personal details of over 2.5 million PlayStation and Xbox users has been hacked on PSP ISO and Xbox ISO forums. These forums aren’t directly linked to the distributors of the gaming counsels…