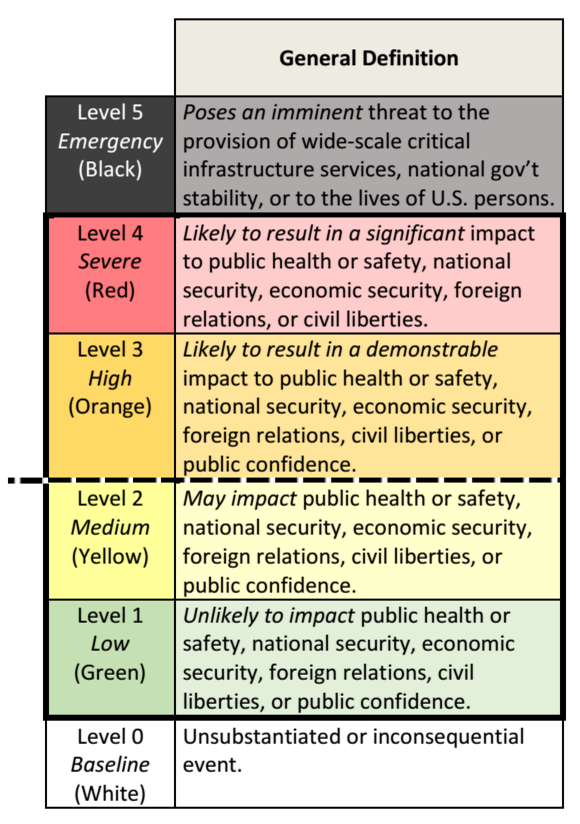
Overview Network security has several moving parts. Of those parts, detection and notification are arguably the most important. Detection/notification are usually the first steps in any security…
On Tuesday (July 26, 2016) the Obama administration released a framework for handling cyberattacks. The Presidential Policy Directive (PPD) on United States Cyber Incident Coordination is a new plan…
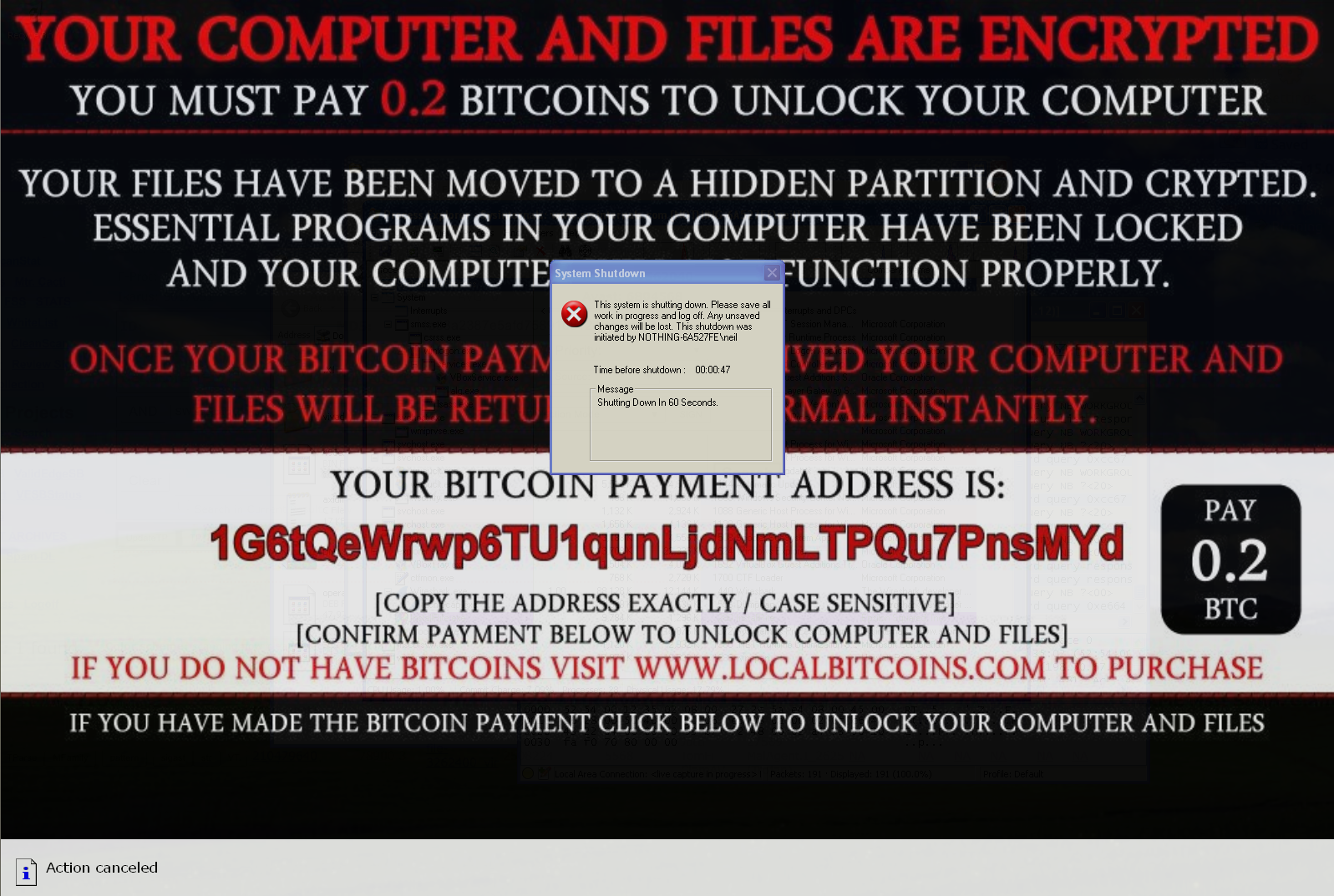
Another week has gone by, and yet another cryptographic ransomware variant has emerged. The latest ransomware discovery has many in the industry concerned because it is rare for a cybercriminal to…
Employee Emergency Notifications
Use PowerShell and Exchange to Notify All Employees through Text Message Do you worry about the safety of your friends, family, and coworkers? It seems like every day there is a report of an active…
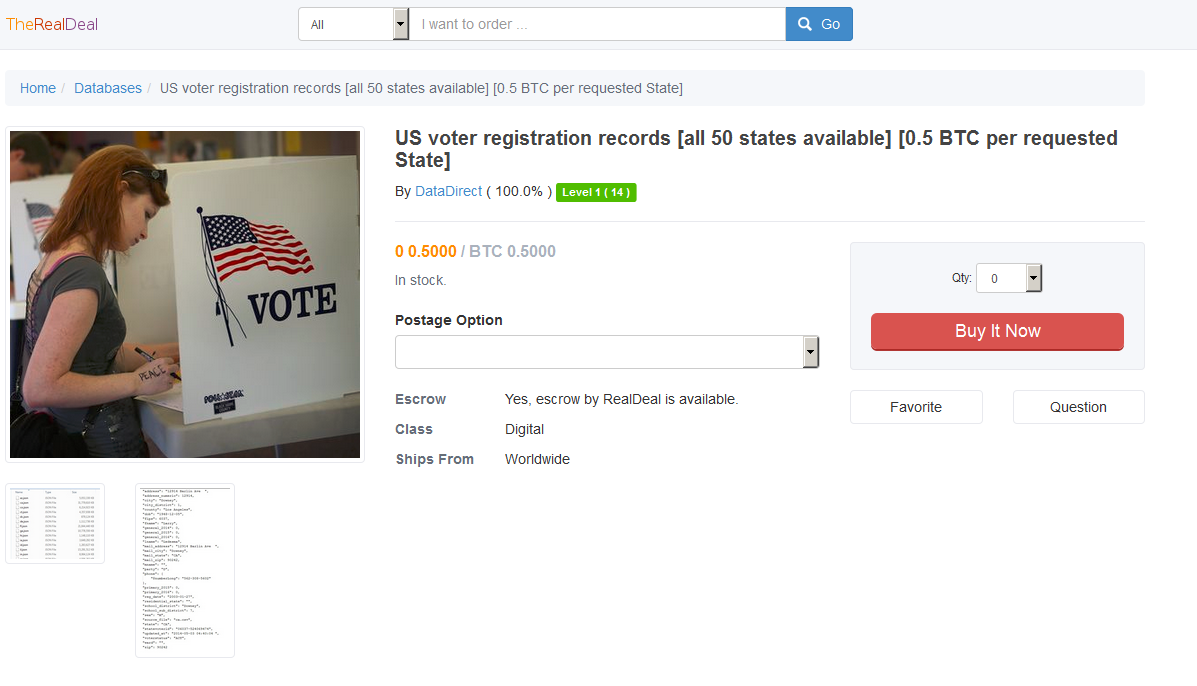
U.S. Voter Registration Database for Sale
As if we do not already have enough to worry about in the upcoming U.S. election, now hackers have access to the entire U.S. Voter Registration database. A seller going by the handle “DataDirect” on…
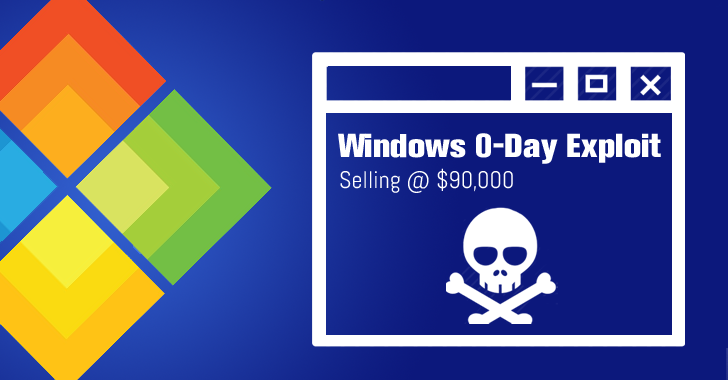
FOR SALE - Zero-Day Exploits
What are Zero-Day Exploits? A zero-day exploit, also known as a zero-day vulnerability, is an unknown exploit that exposes a vulnerability in software or hardware that can create complicated problems…
How Safe Are Your Medical Records?
Hospitals and medical clinics appear to be the biggest target of cyber criminal activity over the last year. According to a study done by Health and Human Services, more than 113 million medical…
This week WatchPoint would like to highlight how you can use NMAP to increase security on your server by closing unused server ports.
Cover-up: FDIC Hacked by Chinese Spies
The Chinese government is believed to have hacked into the Federal Deposit Insurance Corporation (FDIC) in 2010, 2011, and 2013. The House of Representative’s Science, Space and Technology Committee…