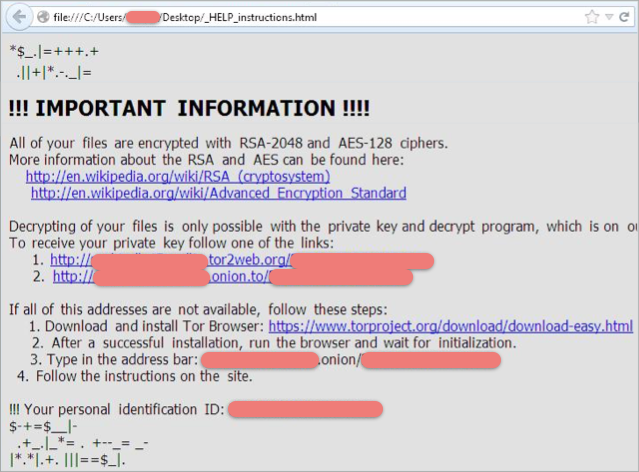
Ransomware is a type of malware that denies access to a device or files until a ransom is paid, at which point the cyber criminals will provide a decryption key to allow the user to regain access to…
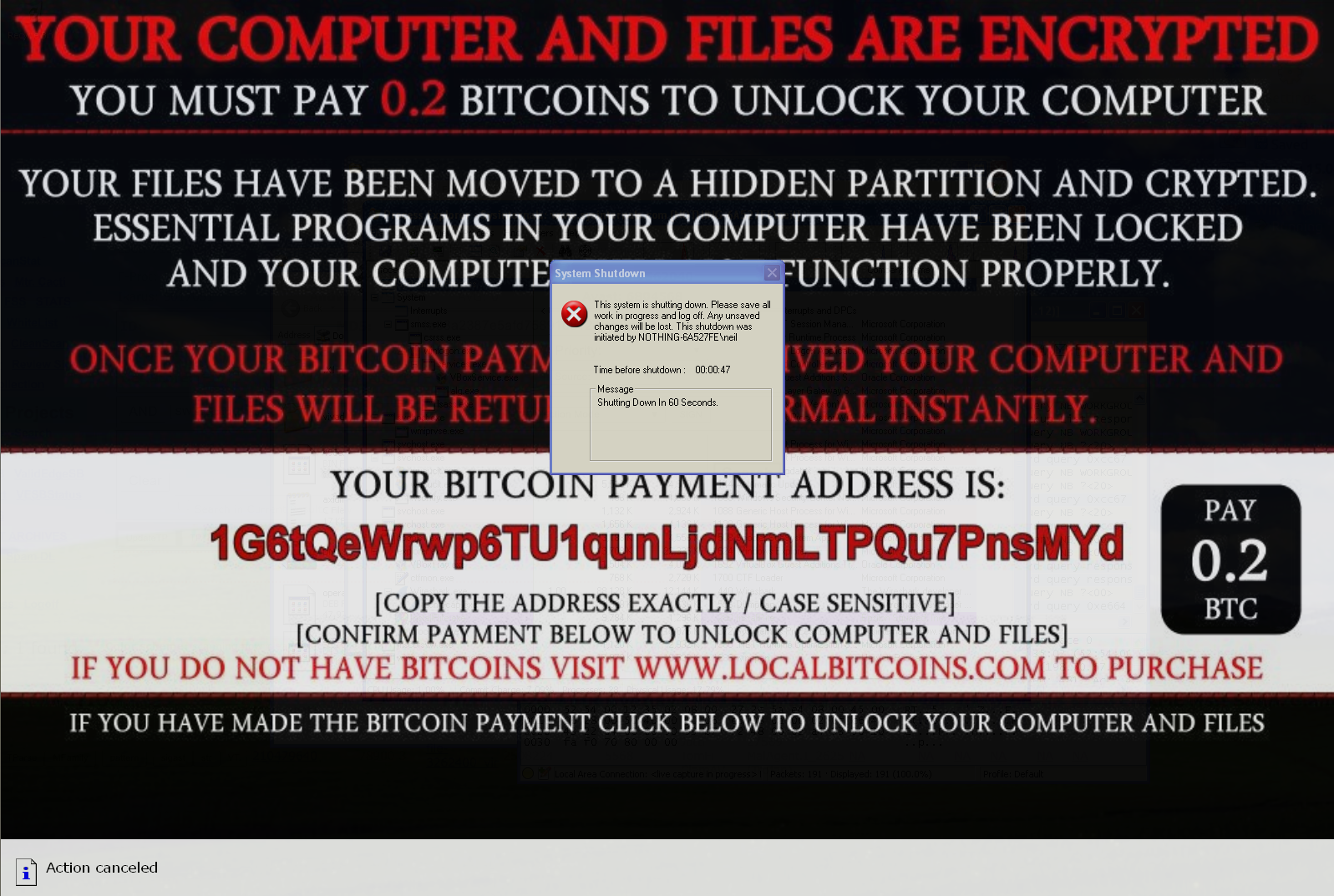
Today we are going to look at how CryptoStopper.io performs against a malware attack by the dreaded TeslaCrypt ransomware. In this demonstration, I will illustrate how quickly a server running…
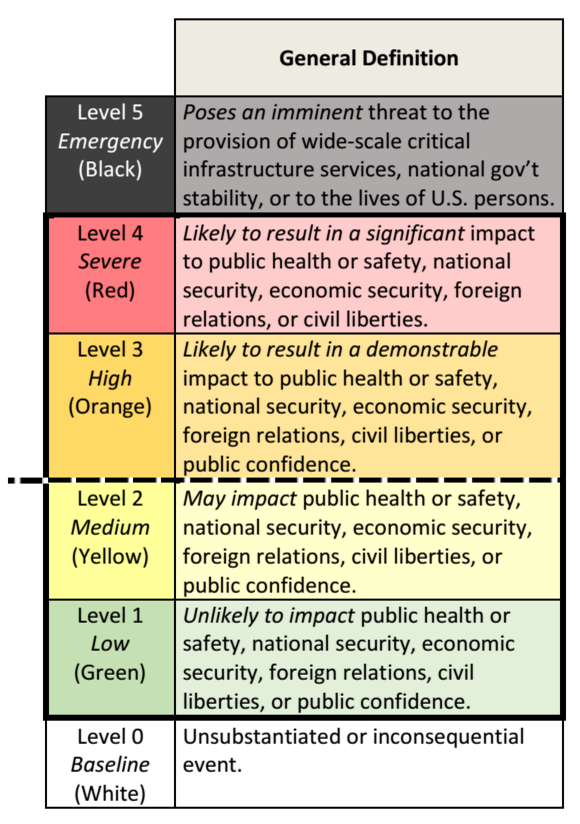
On Tuesday (July 26, 2016) the Obama administration released a framework for handling cyberattacks. The Presidential Policy Directive (PPD) on United States Cyber Incident Coordination is a new plan…
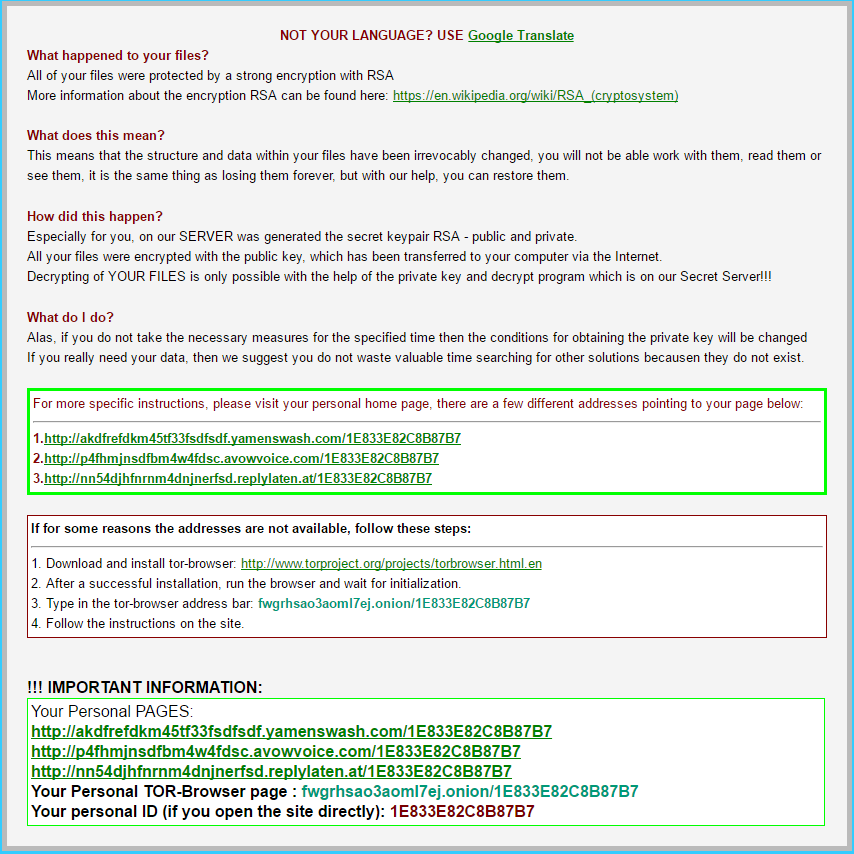
Another week has gone by, and yet another cryptographic ransomware variant has emerged. The latest ransomware discovery has many in the industry concerned because it is rare for a cybercriminal to…
FOR SALE - Zero-Day Exploits
What are Zero-Day Exploits? A zero-day exploit, also known as a zero-day vulnerability, is an unknown exploit that exposes a vulnerability in software or hardware that can create complicated problems…
This week WatchPoint would like to highlight how you can use NMAP to increase security on your server by closing unused server ports.
Zepto Virus - The Newest Form of Ransomware
2016 cyber-crime statistics are on the rise. In the last six months, ransomware infections have increased an alarming 44 percent, and we continue to see new variations every day. Zepto Virus is the…
Back in early January, we gave you a prediction for the Top 7 Cyber Crime Threats for 2016. Now that we are just over half of the way through the year, we thought we would revisit that article and…
What is Deception Technology?
Set a Trap to Catch Cybercriminals Deception Technology is a new approach to cybersecurity that is designed to prevent a cybercriminal who has already infiltrated a network from doing damage. This…